
Are Everyday Tools Quietly Exposing Sensitive Data?
Dec 22, 2025
This week’s newsletter focuses on the quiet mechanics of internal data risk, from daily work patterns to the limits of existing controls.
One Article
This article shows how sensitive data is leaking continuously through everyday tools and workflows, highlighting gaps in visibility, governance, and security controls in most organisations.
One Infographic
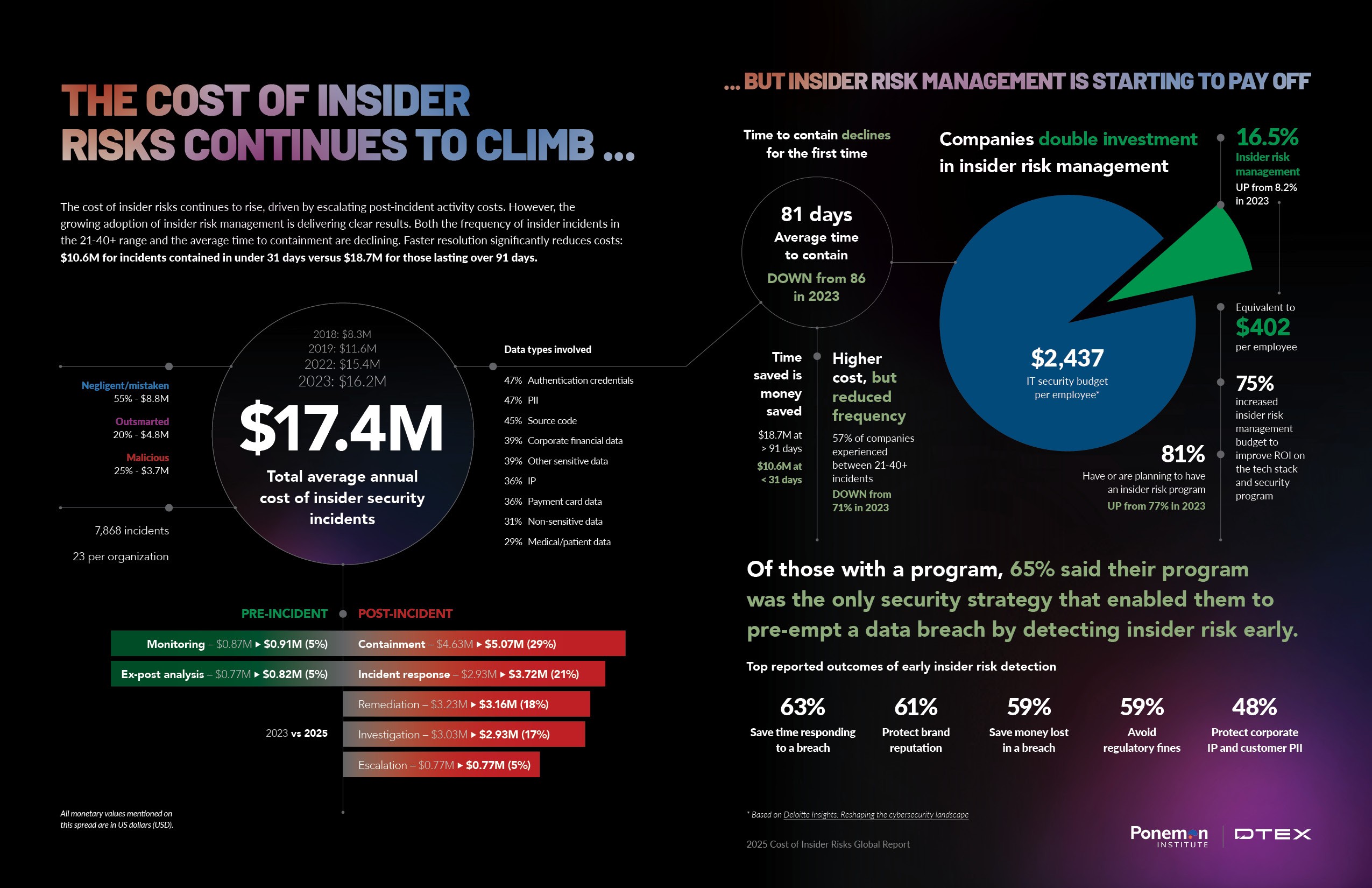
Source: DTEXSystems
One YouTube Video
This video gives a clear introduction to confidential computing and why encryption alone isn’t enough. It explains how trusted execution environments protect data while it’s being processed and why this matters for sensitive workloads.
One Set of Case Studies
This article examines 10 real-world insider threat case studies. By looking at what actually happened, it breaks down how the incidents unfold, why they’re so difficult to prevent, and what practical lessons organisations can take to reduce risk.
One Creative Task
PET ARENA is now live, offering a hands-on way to stress-test privacy in real conditions. The competition invites participants to red-team data-protection mechanisms across a series of missions. Apply to participate now.

